Imagination Product Security Policy
Mission Statement
By promoting open communication and collaboration with security researchers and the community, we strive to build trust, fortify our products, and contribute to the advancement of global cybersecurity standards.
Vulnerability Disclosure Policy
At Imagination Technologies, we take security seriously and appreciate the efforts in identifying and responsibly disclosing potential security vulnerabilities. We are committed to deploying security practices and features at every stage of product development and beyond by actively reviewing potential security vulnerabilities and working with the wider community.
Scope
At Imagination Technologies we are dedicated to fostering a sustainable product security culture by embracing transparency, collaboration, and a commitment to the highest standards.
Our Vulnerability Disclosure Policy and guidelines aim to encourage responsible reporting of vulnerabilities, ensuring swift and effective resolution to protect our customers, partners and end-users.
The Vulnerability Disclosure Policy covers Imagination Technologies HW and SW IP.
Currently Imagination Technologies does not have a bug bounty program.
Guidelines for vulnerability disclosures
To ensure a constructive, transparent and ethical approach we recommend when responsibly disclosing vulnerabilities to refrain from:
- Breaking any applicable law or regulations.
- Accessing unnecessary, excessive or significant amounts of data.
- Modifying data in Imagination Technologies systems or services.
- Attempting or reporting any form of denial of service, e.g. overwhelming a service with a high volume of requests.
- Disrupting Imagination Technologies services or systems.
- Submitting reports detailing non-exploitable vulnerabilities, or reports indicating that the services do not fully align with “best practice”, for example missing security headers.
- Social engineering, ‘phishing’ or physically attacking Imagination Technologies staff or infrastructure.
- Demanding financial compensation in order to not disclose any vulnerabilities.
We expect that you always comply with data protection rules, respect Imagination Technologies’ proprietary information, the privacy of Imagination Technologies’ personnel, and securely delete all research data when it is no longer needed or within one month of the vulnerability being resolved.
This policy is designed to be compatible with common vulnerability disclosure good practice. Both parties will act in good faith to identify and fix security vulnerabilities. It does not give you permission to act in any manner that is inconsistent with the law, or which might cause Imagination Technologies or its partner organisations to be in breach of any legal obligations.
How to submit a vulnerability report
In order to report a potential security vulnerability in any Imagination Technologies Product our preferred method is through our vulnerability reporting form.
Alternatively, you can contact us at [email protected].
When reporting, please provide as much information as possible, including:
- Vulnerability description
- Affected product name (and versions)
- Proof of Concept (PoC) source code to clearly demonstrate the vulnerability
- Description of how the issue was found / reproduced, the impact and any potential remediation
What to expect from Imagination Technologies
Our security response team is the focal point of contacts for reporting security related issues and vulnerabilities. Upon receipt or identification of a vulnerability related issue the security response team will work with teams and SMEs (subject matter experts) within Imagination Technologies following our Security Incident 4-phase approach.
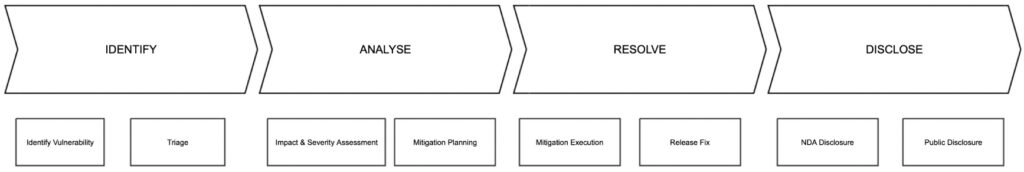
- Identify
- Identify Vulnerability: Potential vulnerabilities from internal or external reporters are logged and the reference ID assigned. At this stage, a uniquely identifiable reference ID will be allocated to the issue.
- Triage: Our initial steps involve conducting comprehensive investigations to validate its authenticity, identifying potential duplicates etc. If the reported issue is found to be not genuine, vexatious, or a duplicate, it will be rejected or marked accordingly.
Our goal is to complete the triage process within 1 week. However, please note that this timeframe may be extended depending on the issue complexity or if further clarification is required from the originator.
- Analyse
- Impact & Severity Assessment: Once we have confirmed the vulnerabilities, an impact and severity assessment will be conducted. At this stage we will notify our security partners and in case the issue does not have a defined “Public Disclosure Date”, we will potentially discuss with relevant parties i.e partner, reporter, CVE authority and agree on a “Public Disclosure Date”.
- Mitigation Planning: Imagination Technologies will develop a mitigation plan or solution to address the confirmed security vulnerability. We strive to provide timely responses and resolutions but timelines may vary based on the complexity of the issue, number of products affected, priority, and release cycles among other factors.
- Resolve
- Mitigation Execution: Imagination Technologies will implement the actions as defined in the mitigation plan.
- Release Fix: Internal development is done at this point and we schedule the fix into a future security package release for our customers
- Disclose
- NDA Disclosure: Customers will be informed at appropriate times, based on the degree to which they’re involved in the mitigation of the vulnerability. Partners that need to assist in development of the mitigation are informed confidentiality at the earliest appropriate time after Triage.
- Public Disclosure: Public Disclosure of vulnerability reports containing relevant information as per the agreed public disclosure date.
Public Disclosure Timelines
Disclosure timelines are determined on a case-by-case basis and with the aim to protect the end user in mind. As a general principle we aim to disclose within a common embargo timeframe of 90 days, although in some cases because of product complexity, mitigation action, development and implementation the embargo period might be longer to enable adequality resolution of vulnerabilities.
In case the vulnerability disclosure date or deadline is due on a weekend or public holiday, the deadline will be moved to the next Imagination Technologies business day.
Security Support Term
The product support term represents the period during which a support for a product is available. The support period for Imagination products may be defined by contractual obligations and internal policies. The period during which a product is considered in-scope for Security Support may or may not coincide with the Support Term.
